Des Key Generation In C

- Des Key Generation In C 1
- Key Generation Software
- Des Key Generation Code In Python
- Des Key Generation Program In C
- Des Key Generation In California
DES Key Generation (K1–K16) 19 64 bit key (including parity-check bits) 28 bits 28 bits Matrix PC-1 and PC-2 are givenby the standard (see nextslide) Ci=LS i(C i-1) Di=LS i(D i-1) Ki=PC-2(CiDi) LS=LeftShift-shift one position if i=1,2,9 or 16-shift two positions otherwise 48 bits. DES works by encrypting groups of 64 message bits, which is the same as 16 hexadecimal numbers. To do the encryption, DES uses 'keys' where are also apparently 16 hexadecimal numbers long, or apparently 64 bits long. However, every 8th key bit is ignored in the DES algorithm, so that the effective key.
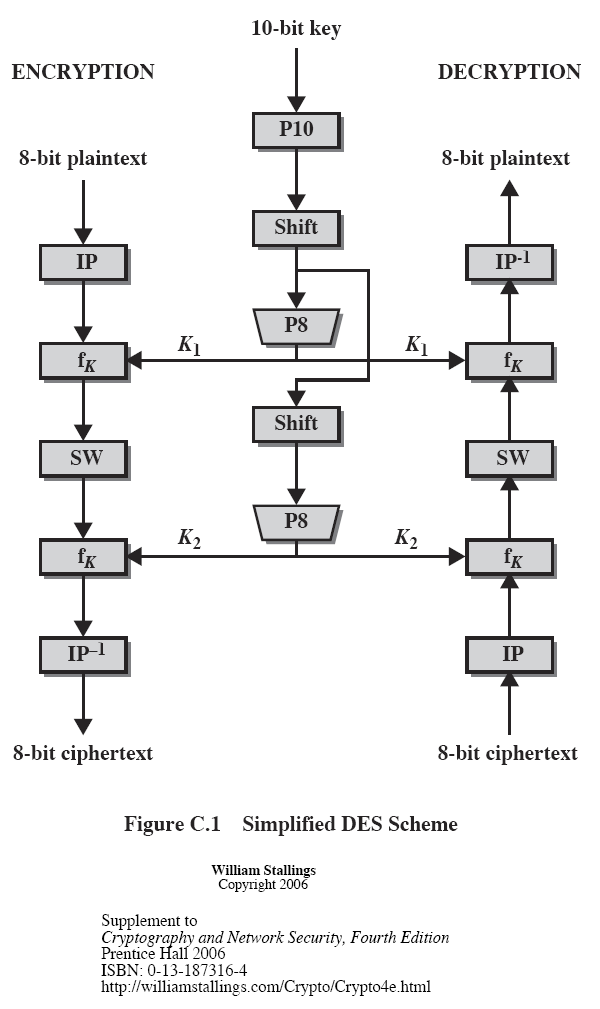
SDES - Simplified DES. Similar properties and structure but with much smaller parameters than DES. As in DES, the initial and final permutations, which are fixed and independent of the key, provide no real security benefit, but make the algorithm slow if implemented in software. Sep 18, 2015 Data Encryption Standard (DES) encrypts blocks of size 64 bit.It was developed by IBM based on the cipher Lucifer under influence of the National Security Agency (NSA).It was a most popular block cipher for most of the last 30 years. By far best studied symmetric algorithm. Nowadays considered insecure due to the small key length of 56 bit.It mainly includes confusion and diffusion. Jan 04, 2018 DES algorithm follows the Feistel Structure Most of the Block cipher algorithms follows Feistel Structure BLOCK SIZE - 64 bits Plain Text No. Of Rounds - 16 Rounds Key Size - 64 bits Sub Key Size. Keyshare Generator emv emv tags tlv decoder cap calculator cryptogram calc crypto des calc asn1 decoder banking pin translation keyshare tools misc hex dump char converter research banking t&c pin usage relay attack sca in psd2. The KCV is the 'Key Check Value' for the key, calculated by assuming the key/components are 3DES keys,. Example C Program: Creating a Key Container and Generating Keys.; 3 minutes to read; In this article. The following example creates a named key container and adds a signature key pair and an exchange key pair to the container. This example can be run without problem even if the named key container and cryptographic keys already exist.
This is a program for Encryption and Decryption
This program uses the Simple Data Encryption Standard (SDES) Algorithm.
This Algo takes 8-bits of plaintext at a time and produces 8-bits of ciphertext.
It uses 10-bits of key for Encryption and Decryption.
I have extreme interest in learning new Technologies.
Currently working in IPTV Domain. Its cool!
Udupa
sir..Can I get explaination for each line please..
Thank you in advance
Mocabilly14
@Sri_2
It's C language.
See the fragment with the includes. typical for C.
Don't know if it's ansi-C or C++ or an other 'version' of C..
A cool program for sure, but I always submit to the observation I have read in a practical crypto book, 'Don't roll your own encryption' I don't know much about this crypto standard, but when people roll their own encryption they tend to make mistakes regaurdless of how well they try. There shouldy be crypto analysts, and mathemeticians, and whole scores of other people involved in implementing a crypto standard. More eyes take care of the problems. Subtle problems are always the bane of crypto programs.
Des Key Generation In C 1
-->The following example creates a named key container and adds a signature key pair and an exchange key pair to the container. This example can be run without problem even if the named key container and cryptographic keys already exist.
Note
I tried calling Microsoft and the people who answered their phone didn't even know what Frontpage was (seriously). Windows 2003 r2 product key generator. Mine isnt working right and my parents cant afford another one.I lost the original case to my Frontpage 2003 and none of the codes listed worked.
An application should not use the default key container to store private keys. When multiple applications use the same container, one application may change or destroy the keys that another application needs to have available. It is recommended that applications use key containers that are linked to the application. Doing so reduces the risk of other applications tampering with keys that are necessary for an application to function properly.
This example demonstrates the following tasks and CryptoAPI functions:
- It attempts to acquire the named key container. If the named key container does not already exist, it is created.
- If a signature key pair does not exist in the key container, it creates a signature key pair within the key container.
- If an exchange key pair does not exist in the key container, it creates an exchange key pair within the key container.
Key Generation Software
These operations only need to be performed once for each user on each computer. If the named key container and key pairs have already been created, this sample performs no operations.
Des Key Generation Code In Python
This example uses the following CryptoAPI functions:
Des Key Generation Program In C
Des Key Generation In California
This example uses the function MyHandleError. The code for this function is included with the sample. Code for this and other auxiliary functions is also listed under General Purpose Functions.