32 Bit Hex Encryption Key Generator
- 32 Bit Hex Encryption Key Generator Free
- 256 Bit Encryption Key Generator
- 32 Bit Hex Encryption Key Generator Download
- 32 Bit Hex Encryption Key Generator Download
Web app offering modular conversion, encoding and encryption online. Translations are done in the browser without any server interaction. This is an Open Source project, code licensed MIT. WinHex App for Windows 10 PC: WinHex (2020) latest version free download for Windows 10. Install WinHex full setup 64 bit and 32 bit on you PC. 100% safe and free download from Softati.com. Computer Forensics & Data Recovery Software, Hex Editor & Disk Editor. Is there any way or sample through which we can acheive AES Encrypt using 256 bit hex key. Also what are the specifications for a 256 bit hex key. (also does it have to do with the character length).
- No there isn't. @MartinPrikryl 'There's always (automatically generated) client-side key pair, even with password authentication.' Asymmetric crypto keypairs are only used for authentication, not establishing a secure channel.' Filezilla sftp generate public key.
- Online RSA key generation: RSA (Rivest, Shamir and Adleman) is an asymmetric (or public-key) cryptosystem which is often used in combination with a symmetric cryptosystem such as AES (Advanced Encryption Standard).
- Online RSA Key Generator. Key Size 1024 bit. 512 bit; 1024 bit; 2048 bit; 4096 bit Generate New Keys Async. RSA Encryption Test. Text to encrypt: Encrypt / Decrypt.
40-bit encryption refers to a key size of forty bits, or five bytes, for symmetric encryption; this represents a relatively low level of security. A forty bit length corresponds to a total of 240 possible keys. Although this is a large number in human terms (about a trillion), it is possible to break this degree of encryption using a moderate amount of computing power in a brute-force attack, i.e., trying out each possible key in turn.
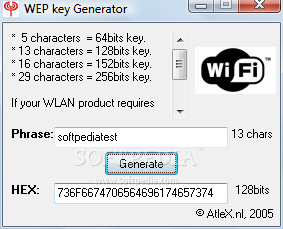
The Firewall.cx Wireless LAN Key Generator will allow the generation of a WEP or WPA ASCII based encryption key and will provide the equivalent HEX or ASCII string so it can be inserted directly into a Cisco Access Point configuration. Using 32 hexadecimal digits vs ASCII equivalent 16-character password. From which you derive a 128 bit key for 128-bit AES encryption. Here the entropy is reduced.
Description[edit]
A typical home computer in 2004 could brute-force a 40-bit key in a little under two weeks, testing a million keys per second; modern computers are able to achieve this much faster. Using free time on a large corporate network or a botnet would reduce the time in proportion to the number of computers available.[1] With dedicated hardware, a 40-bit key can be broken in seconds. The Electronic Frontier Foundation's Deep Crack, built by a group of enthusiasts for US$250,000 in 1998, could break a 56-bit Data Encryption Standard (DES) key in days,[2] and would be able to break 40-bit DES encryption in about two seconds.[3]
40-bit encryption was common in software released before 1999, especially those based on the RC2 and RC4 algorithms which had special '7-day' export review policies,[citation needed] when algorithms with larger key lengths could not legally be exported from the United States without a case-by-case license. 'In the early 1990s .. As a general policy, the State Department allowed exports of commercial encryption with 40-bit keys, although some software with DES could be exported to U.S.-controlled subsidiaries and financial institutions.'[4][5] As a result, the 'international' versions of web browsers were designed to have an effective key size of 40 bits when using Secure Sockets Layer to protect e-commerce. Similar limitations were imposed on other software packages, including early versions of Wired Equivalent Privacy. In 1992, IBM designed the CDMF algorithm to reduce the strength of 56-bit DES against brute force attack to 40 bits, in order to create exportable DES implementations.
Obsolescence[edit]
32 Bit Hex Encryption Key Generator Free
All 40-bit and 56-bit encryption algorithms are obsolete, because they are vulnerable to brute force attacks, and therefore cannot be regarded as secure.[6][7] As a result, virtually all Web browsers now use 128-bit keys, which are considered strong. Most Web servers will not communicate with a client unless it has 128-bit encryption capability installed on it.
Public/private key pairs used in asymmetric encryption (public key cryptography), at least those based on prime factorization, must be much longer in order to be secure; see key size for more details.
As a general rule, modern symmetric encryption algorithms such as AES use key lengths of 128, 192 and 256 bits.
See also[edit]
Footnotes[edit]
- ^Schneier 1996, p. 154.
- ^EFF-1998.
- ^Schneier 1996, p. 153.
- ^Grimmett 2001.
- ^Schneier 1996, p. 615.
- ^University of California at Berkeley Public Information Office (January 29, 1997). 'The only legally exportable cryptography level is totally insecure; UC Berkeley grad student breaks challenge cipher in hours'. The Regents of the University of California. Retrieved December 14, 2015.
This is the final proof of what we've known for years: 40-bit encryption technology is obsolete.
- ^Fitzmaurice, Ellen; Tamaki, Kevin (June 1, 1997). 'Decoding the Encryption Debate: U.S. export restrictions and 'key recovery' policies are ineffectual as well as burdensome to business'. Los Angeles Times. Retrieved December 14, 2015.
But recent advances in computing technology have rendered 40-bit encryption dangerously weak and export limits commercially obsolete.
References[edit]
- 'Frequently Asked Questions (FAQ) About the Electronic Frontier Foundation's 'DES Cracker' Machine'. Electronic Frontier Foundation. July 16, 1998. Archived from the original on September 18, 2012. Retrieved March 23, 2012.
- Grimmett, Jeanne J. (2001). Encryption Export Controls(pdf) (Report). Congressional Research Service Report RL30273.
- Schneier, Bruce (1996). Applied Cryptography (Second ed.). John Wiley & Sons. ISBN0-471-11709-9.
Advanced Encryption Standard(AES) is a symmetric encryption algorithm. AES is the industry standard as of now as it allows 128 bit, 192 bit and 256 bit encryption.Symmetric encryption is very fast as compared to asymmetric encryption and are used in systems such as database system. Following is an online tool to generate AES encrypted password and decrypt AES encrypted password. It provides two mode of encryption and decryption ECB and CBC mode. For more info on AES encryption visit this explanation on AES Encryption.
Also, you can find the sample usage screenshot below:
If You Appreciate What We Do Here On Devglan, You Can Consider:
- Like us at: or follow us at
- Share this article on social media or with your teammates.
- We are thankful for your never ending support.

Usage Guide
Any plain-text input or output that you enter or we generate is not stored on this site, this tool is provided via an HTTPS URL to ensure that text cannot be stolen.
Generator product key office 2013. Jan 26, 2020 The Microsoft Office 2013 Product Key Generator is a free tool that is used to generate the activation keys for Microsoft Office 2013 for life. It must be the activation process after installing Microsoft Office 2013, but don’t worry, there is a tremendous tool that is used for the activation of Microsoft Products.
For encryption, you can either enter the plain text, password, an image file or a .txt file that you want to encrypt. Now choose the block cipher mode of encryption. ECB(Electronic Code Book) is the simplest encryption mode and does not require IV for encryption. The input plain text will be divided into blocks and each block will be encrypted with the key provided and hence identical plain text blocks are encrypted into identical cipher text blocks. CBC mode is highly recommended and it requires IV to make each message unique. If no IV is entered then default will be used here for CBC mode and that defaults to a zero based byte[16].
The AES algorithm has a 128-bit block size, regardless of whether you key length is 256, 192 or 128 bits. When a symmetric cipher mode requires an IV, the length of the IV must be equal to the block size of the cipher. Hence, you must always use an IV of 128 bits (16 bytes) with AES.
AES provides 128 bit, 192 bit and 256 bit of secret key size for encryption. Things to remember here is if you are selecting 128 bits for encryption, then the secret key must be of 16 bits long and 24 and 32 bits for 192 and 256 bits of key size. Now you can enter the secret key accordingly. By default, the encrypted text will be base64 encoded but you have options to select the output format as HEX too.
Similarly, for image and .txt file the encrypted form will be Base64 encoded.
Below is a screenshot that shows a sample usage of this online AES encryption tool.
256 Bit Encryption Key Generator
AES decryption has also the same process. By default it assumes the entered text be in Base64. The input can be Base64 encoded or Hex encoded image and .txt file too. And the final decrypted output will be Base64 string. If the intended output is a plain-text then, it can be decoded to plain-text in-place.
32 Bit Hex Encryption Key Generator Download
But if the intended output is an image or .txt file then you can use this tool to convert the base64 encoded output to an image.
Please enable JavaScript to view the comments powered by Disqus.